GPU-Assisted Malware Can Be Difficult to Detect
A proof-of-concept code shows that malware may get really nasty in the near future.

Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
While GPUs bring parallel processing and superior graphics to the PC, they can also be tools for malicious purposes.
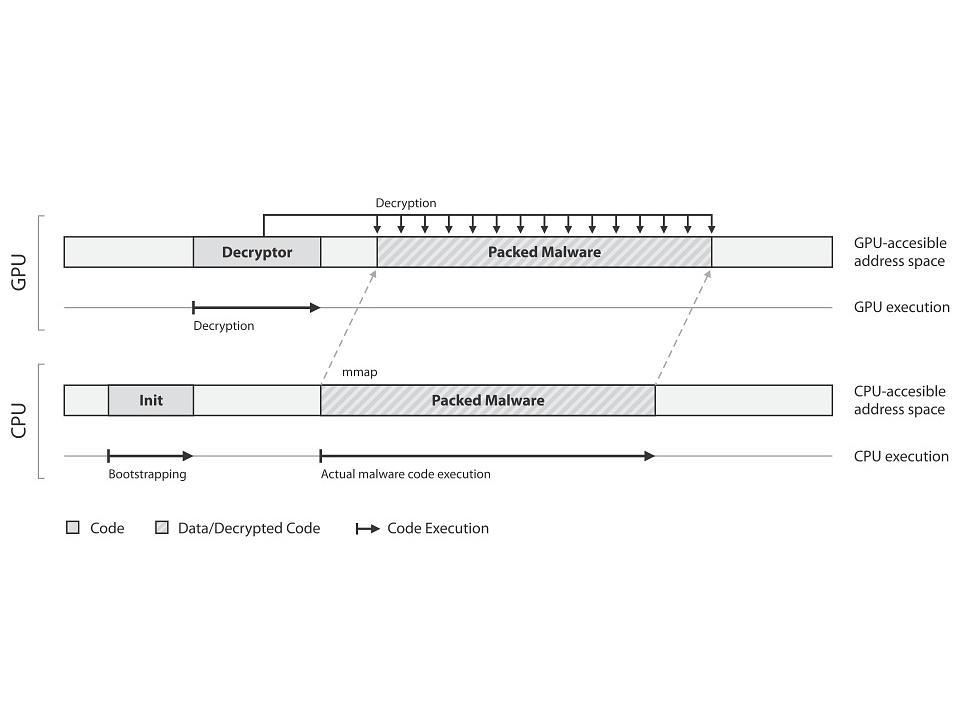
According to a research paper entitled GPU-Assisted Malware, a team of scientists from Greece and the U.S. has developed proof-of-concept code that dumps malware components onto the GPU during the "unpacking" process of an executed malicious file, evading traditional security defenses.
Typically self-unpacking methods are used to evade signature-based anti-virus scanning, as they allow the hacker to make changes to the compression or encryption when needed without altering the entire package, making the hidden payload hard to detect. However these methods required access to the PC's CPU which in turn presents limitations. Now hackers can conceivably use the GPU to create even more complex encryption schemes that wouldn't be possible solely on a CPU.
"Implementing the self-unpacking functionality of a malware binary using GPU code can pose significant obstacles to current malware detection and analysis systems,” the scientists wrote in the research paper. "A malware author can take advantage of the computational power of modern graphics processors and pack the malware with extremely complex encryption schemes that ... can be efficiently computed due to the massively parallel architecture of GPUs."
The paper explains that the malicious code--once its unpacked by the GPU--is placed into a memory location accessible by the CPU, and then executed by the CPU. This process calls for the majority of the code to be written for the GPU, leaving little to be used on Intel's x86 chip architecture, and leaving a rather small footprint in the system memory. This means that current security solutions will have an even harder time detecting malicious activity.
To make matters worse, GPU-assisted malware will make it even more difficult for security researchers to reverse-engineer and analyze thanks to the GPU's ability to decode and re-encode segments of the virus more quickly. "Although complete extraction of the original code is still possible by a determined malware analyst, when combined with existing anti-debugging techniques, this form of GPU-assisted polymorphism makes the whole reverse engineering process a challenging and time-consuming task,” the paper states.
To learn more about the proof-of-concept code, read the PDF file here. The team plans to fully disclose its findings next month at the IEEE's International Conference on Malicious and Unwanted Software.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Kevin started taking PCs apart in the 90s when Quake was on the way and his PC lacked the required components. Since then, he’s loved all things PC-related and cool gadgets ranging from the New Nintendo 3DS to Android tablets. He is currently a contributor at Digital Trends, writing about everything from computers to how-to content on Windows and Macs to reviews of the latest laptops from HP, Dell, Lenovo, and more.
-
duzcizgi mayankleoboy1assholes just gave an idea to the hackersReply
Considering there are about 6 billion people in the world and also considering that the hackers have all above average education and intelligence, this paper is not giving them any new ideas but just warning the rest of the community on this possiblitiy.
As the paper states, it is nearly impossible to detect such a malware with the conventional methots that we all use in our current "security suites" that we pay subscription for security of our computer.
In short, there's no guarantee that someone already exploited this (if I was a malware author, I'd have silently used it and shut my mouth) but none of our antivirus/antimalware programs were able to even detect its presence! -
Rancifer7 I wonder how well it will unpack on the massively parallel integrated Intel graphics?Reply
Maybe now the malware can play Crysis.. -
g00fysmiley rhino13Here we go!One more feature of my system Norton will kneecap.Reply
somebody on tom's uses norton? >_< move past the bloatware. avg free or something.. really almost anything (short of macafee) will be less full of bloatware -
bear_jesus would gpu load not give it away, for one would the gpu not go from idle clock speeds to loaded speeds and also from 0% load to anything above it?Reply
 Club Benefits
Club Benefits










