Internet
Explore Internet
Latest about Internet

Best online fax services
By Melissa Perenson last updated
Check out our full reviews of the best online fax services before picking one to securely and affordably transfer your documents.
VPN vs proxy: what's the difference and which should you get?
By Mo Harber-Lamond last updated
VPN VPN and proxies perform similar tasks, but in practice they're very different. Here we run down what each does and how to choose.
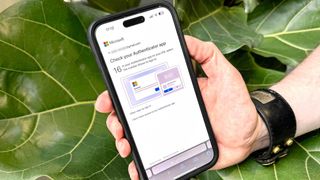
How to set up two-factor authentication for your Microsoft account
By Josh Render published
This guide will help you set up two-factor authentication for your Microsoft account, including downloading and setting up the Microsoft Authenticator app

Best TikTok VPN: evade bans and access anywhere
By Mo Harber-Lamond last updated
VPN Skepticism of TikTok has reached an all-time high, and demand for TikTok VPN services is rapidly rising. Here are the ones we trust the most.

TikTok ban gets real in US as bill passes Senate — and Biden just signed it
By Dave LeClair published
The US Senate passed a bill forcing TikTok's parent company to sell the app or be banned in the United States.

The best China VPN: working services in 2024
By Mo Harber-Lamond last updated
VPN A China VPN is essential for anyone traveling to the country – but not every provider works. Here are the very best VPNs for China on the market.

The best ad blockers in 2024
By John Corpuz last updated
The best ad blockers and privacy extensions will banish intrusive ads and help you opt out of invasive tracking online.

The best Mac VPN in 2024
By Mo Harber-Lamond last updated
Updated A VPN for Mac should be able to do it all – privacy, streaming, and speed. Here are the best Mac VPNs, including ExpressVPN, NordVPN, and Surfshark.
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.


