Security
Latest about Security

New study reveals Chrome is bad for your privacy but it's not the worst browser
By Scott Younker published
Web browsers are one of the most essential tools we rely on everyday but it turns out they're also putting our privacy at risk.

3.5 million hit in US college data breach with full names, dates of birth, SSNs, bank info and more exposed — how to see if you’re affected
By Anthony Spadafora published
The University of Phoenix has suffered a data breach after the Clop ransomware gang stole data from the university’s network earlier this year.

7 security steps to prepare your home before you leave your for the holidays
By Amber Bouman published
Take these seven security steps before you head out for the holidays to ensure your home is protected while you're gone.

Nearly 2 million Android devices hijacked by massive new botnet — how to stay safe
By Amber Bouman last updated
A large-scale botnet has taken over millions of Android devices in order to use them for nefarious purposes.

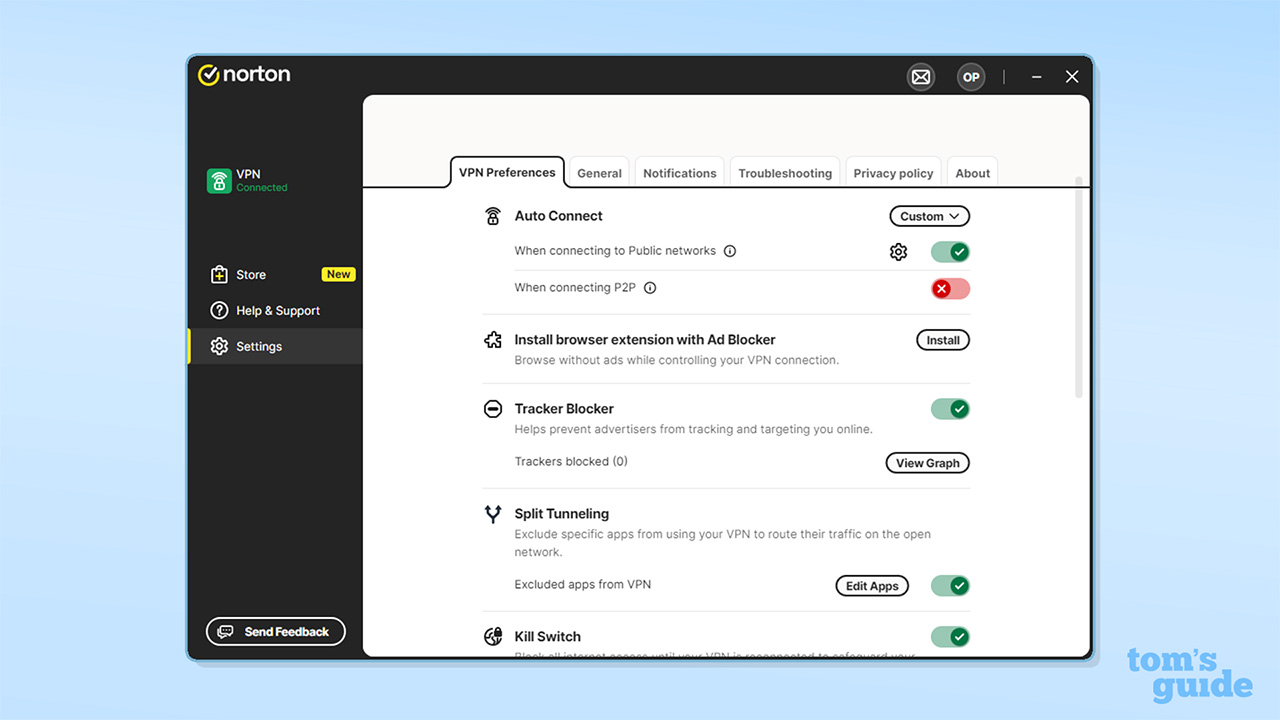
The fastest VPN services in 2025
By Olivia Powell last updated
We've tested dozens of VPNs to determine the top 5 fastest VPNs, including Proton VPN, NordVPN and Surfshark

The best streaming VPN in 2025
By Olivia Powell last updated
VPN We've tested dozens of VPNs with streaming sites like Netflix and BBC iPlayer to bring you a definitive ranking of the top 5 best streaming VPNs, including NordVPN, Surfshark and ExpressVPN

The best free VPN in 2025
By Mo Harber-Lamond last updated
Most free VPNs are useless – but there are a few that are worth considering. This is our tested and ranked guide to the only free VPN services we recommend.

Microsoft accounts are under attack by hackers - here's how to stay safe from this age-old tactic
By Amber Bouman last updated
Microsoft accounts are being targeted using a common hacking technique which purposefully misspells websites and email addresses.
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!