android
Latest about android

Best Android phones 2024
By Philip Michaels last updated
Our list of the best Android phones at every size and for every budget will help you make the right choice.

The best ad blockers in 2024
By John Corpuz last updated
The best ad blockers and privacy extensions will banish intrusive ads and help you opt out of invasive tracking online.
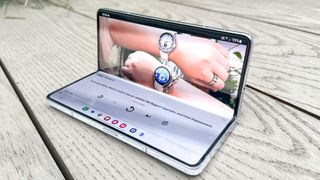
Samsung Galaxy Z Fold 6 and Flip 6 color and storage options leaked — what we know
By Scott Younker published
The latest leaks for the Galaxy Z Fold 6 and Z Flip show off new colorways and confirm storage capacities for both foldables.

Pixel 8a — 5 biggest rumored upgrades
By John Velasco published
Ahead of its potential announcement at Google I/O, we break down all of the biggest rumored upgrades coming to the Google Pixel 8a.

Android phones are getting a powerful parental control upgrade
By Alan Martin published
Google appears to be planning on introducing a way of requiring parental consent before a child can message someone.

New Google Pixel 9 Pro leak just revealed major design changes
By Scott Younker published
The latest leaked images of the Google Pixel 9 Pro show a smaller device with some interesting cosmetic changes.

Best running apps for 2024
By Jane McGuire last updated
We've tried out the best running apps and rounded up our favorites. Here's what our runners think.

Android and Pixel teams merge in major AI push but analyst sees a danger
By Scott Younker last updated
It's all about speeding up AI integration without alienating partners
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.

