News
Latest News
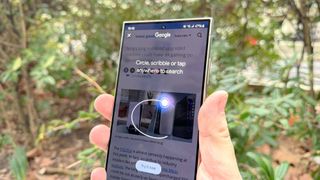
Circle to Search could be adding another feature — and I couldn't be happier
By Philip Michaels published
Code related to Circle to Search reveals the Galaxy AI tool could add the ability to create and share screenshots. It would be a welcome addition to what's already a helpful feature.

5 top new movies to stream this week on Netflix, Shudder and more April (23-29)
By Rory Mellon published
"Anyone But You", "Miller's Girl" "Monkey Man" and more unmissable new movies make their streaming debut this week

Tour de Romandie 2024: live stream cycling online
By Simon Warren published
Watch the Tour de Romandie 2024 for a host of star riders making final preparations to their form before the Giro.

Meta announces Quest OS open headset platform — Xbox, Asus and Lenovo are first partners
By Scott Younker published
Meta is licensing the Quest headset operating system to hardware manufacturers beginning with Asus and Lenovo.

Target stops selling Blu-Ray movies — here’s where you can still get them
By Scott Younker published
Target says it's moving away from DVDs, including Blu-Ray movies, with plans to only carry the physical media at select times like holidays or major releases.

Arsenal vs Chelsea live stream: How to watch Premier League game online
By Charlotte Henry published
The Arsenal vs Chelsea live stream is a huge London derby in the Premier League as the Gunners try to stay top. Here's how to watch from anywhere.

Best cheap OLED TV deals for April 2024
By Louis Ramirez last updated
OLED TV deals aren't easy to find. So we're rounding up today's best cheap OLED TV deals.

Best cheap TV deals in April 2024
By Louis Ramirez last updated
The best cheap TV deals you can buy from major retailers like Best Buy, Walmart, Amazon, and more.
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.


