Crazy Britney Spears Malware Is Toxic — and Criminal
The command-and-control server for a new piece of Russian malware is hidden in plain sight: right on Britney Spears' Instagram page.

Britney Spears the pop icon may have come and gone, but Britney Spears the malware magnet is alive and well.
A group of Russian hackers — possibly working at the behest of the Russian government — has been distributing a malicious Firefox extension, which can draft compromised computers into a botnet. The twist: The command-and-control server pulling the strings of the infected machines is hidden in plain sight, right on Britney Spears's Instagram page. Talk about being a Slave 4 U.
Information comes from WeLiveSecurity, a blog from Bratislava, Slovakia-based security firm ESET. The ESET researchers were looking into Turla, a Russian cyberespionage outfit that has been targeting governments and government officials all around the world for two decades.
MORE: Best Antivirus Software and Apps
Turla's latest attack involves a shady Firefox extension called HTML Encoding 0.3.7, which ESET discovered on a compromised Swiss website. The website's usual users, Turla reasoned, would download and install the innocuous-sounding extension, then become part of Turla's botnet. At that point, Turla could leverage computers within the botnet to wreak further havoc, from stealing private information to launching denial-of-service attacks.
Botnets through questionable browser extensions are a dime a dozen; what's more interesting is how HTML Encoding 0.3.7 accesses its command-and-control server. Instead of using hyperlinks — which would give away the server's location as soon as researchers discovered it — they hid it in plain sight, in a location that's not only legitimate, but downright popular.
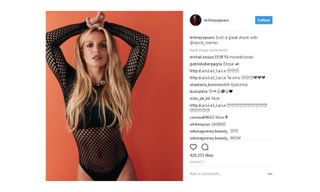
One photo on the official Britney Spears Instagram page shows the pop singer in a skimpy fishnet getup, striking an attractive pose. User asmith2155 commented, "#2hot make loved to her, uupss #Hot #X." It's not the most cogent comment, granted, but it's not radically different from thousands of other half-coherent ramblings on other celebrity Instagram posts.
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.
The comment isn't as nonsensical as it seems, though. HTML Encoding 0.3.7 will bring users to Britney's Instagram photo, then compute a unique hash value for each comment. If it finds a value that matches 183, it will convert the comment into a URL. The "#2hot" comment converts into a bit.ly link that takes users directly to the command-and-conquer server. From there, their computers are no longer fully their own.
There's some good news for Britney Spears fans, though. First off, you have to download the compromised Firefox add-on before you're at risk, and you're not likely to do that unless Turla is actively targeting your government. (You're also not likely to do it if you follow common sense safety protocols online.)
Furthermore, the C&C server’s website has only 17 recorded hits, suggesting that the Turla team may have just been running a test (or that no one fell for their Firefox extension). Here's hoping they soon give up and leave Britney alone.
In other words, you can hit that Instagram one more time without cause for concern.
Marshall Honorof is a senior editor for Tom's Guide, overseeing the site's coverage of gaming hardware and software. He comes from a science writing background, having studied paleomammalogy, biological anthropology, and the history of science and technology. After hours, you can find him practicing taekwondo or doing deep dives on classic sci-fi.

