Security
Latest about Security

Millions of Discord users being tracked by spy site — what you need to know
By Anthony Spadafora published
Discord users could be at risk online after a data-scraping service was set up last year to harvest their messages and track them across the web.

The best WhatsApp alternatives for 2024
By Tom Pritchard last updated
It doesn't matter why you'd want to leave, but these best WhatsApp alternatives mean you have somewhere to go.

The best VPN service in 2024
By Mo Harber-Lamond last updated
Updated I've tested hundreds of the best VPN services. Here I compare the top 10, including NordVPN, ExpressVPN, Surfshark and more.
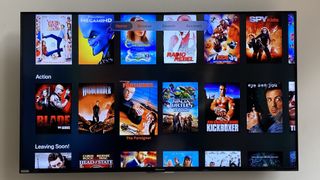
How to watch overseas content with a VPN
By Olivia Powell last updated
vpn If geo-blocking is preventing you from watching your favorite shows, learn how to use a VPN to watch content from overseas.

AI-generated voice scams on the rise — 5 tips to protect yourself and your family
By Josh Render published
AI-based scams focus on using voices that are easily findable online. However, here are five tips to help you protect yourself and your family.

The best Australia VPN in 2024
By Olivia Powell last updated
VPNs down under Whether you live Down Under or you're just visiting, an Australia VPN is the easiest way to access more streaming content and stay safe online.

The best gaming VPN in 2024
By Mo Harber-Lamond last updated
VPN A gaming VPN is the simplest solution to avoiding DDoS attacks and network throttling. Here are my top 5, including NordVPN, ExpressVPN and Surfshark.

The best Valorant VPN in 2024: use global servers and unblock VoIP anywhere
By Mo Harber-Lamond last updated
VPN Can't access all the features of Valorant in your country? Simply download the best Valorant VPN to use VoIP and stay safe from DDoS attacks.
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.


