android
Latest about android

Android phones are getting a powerful parental control upgrade
By Alan Martin published
Google appears to be planning on introducing a way of requiring parental consent before a child can message someone.

New Google Pixel 9 Pro leak just revealed major design changes
By Scott Younker published
The latest leaked images of the Google Pixel 9 Pro show a smaller device with some interesting cosmetic changes.

Best running apps for 2024
By Jane McGuire last updated
We've tried out the best running apps and rounded up our favorites. Here's what our runners think.

Android and Pixel teams merge in major AI push but analyst sees a danger
By Scott Younker last updated
It's all about speeding up AI integration without alienating partners

Samsung Galaxy A35 5G hands-on review: The Pixel 7a has a lot to be worried about
By John Velasco published
Not yet rated$399 on paper looks mighty tempting

This is the Google Pixel 8a in every color and every angle — thanks to new leak
By Scott Younker published
Newly leaked images seem to confirm the four color options for the Pixel 8a, while giving us a complete look at Google's upcoming phone.
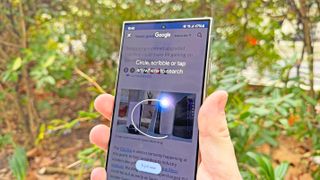
Samsung Galaxy S24's best feature could soon get a big usability upgrade
By Richard Priday published
Google Pixel and Samsung Galaxy phones' Circle to Search feature could get some usability upgrades according to statements made on a Made by Google Podcast episode.

The Pixel 9 could get this long-overdue upgrade to fix cellular connectivity issues
By Alyse Stanley published
Google's Pixel 9 series is set to receive a modem upgrade that would add support for satellite connectivity, according to a new report.
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.


