Lost Bitcoins? Don't Click on This Malware Spam
Don't compound the pain of losing your digital shirt by clicking on this malware-laden link that promises to recover lost bitcoins.


Have you lost money in the collapse of Bitcoin exchange Mt. Gox? Are you hoping to get some of it back? Then you're the perfect target for a new malware-distributing spam campaign.
"I've noticed a scam mail that is going around the Internet recently claiming that Mt. Gox has decided to return customers their bitcoins," posted Reddit user "strongleaf" yesterday (March 3). "It goes by, 'Have you lost your MTGOX Coins? Go watch our news to claim your Bitcoins back!'"
MORE: Mt. Gox Bankruptcy: What Bitcoin Owners Need to Know
The email message then displays a link to a page on the website "bitcoinbreaknews [dot] com." That page has since been removed, but the website is still up — its front page mimics the video-player index page of The Wall Street Journal website, complete with working videos.
However, the main video screen on the fake WSJ site is replaced by a pop-up window that asks you to "install Adobe Flash Player." You can bet your bottom bitcoin that it doesn't install the real Flash Player.
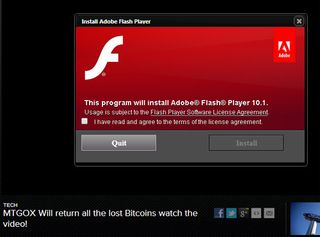
"Clicking the Install button downloads a .rar file," a type of compressed archive, wrote Malwarebytes researcher Chris Boyd in a company blog post. (Real Adobe Flash Player installers are regular Windows ".exe" files.)
The original Reddit poster downloaded and opened the archive and saw three files being extracted: a fake version of Adobe Flash Installer, a license file and a README file.
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.
"After clicking onto the malicious Adobe_Flash_Installer.exe, the file will immediately disappear," wrote strongleaf.
"It is apparent that the malware has installed onto the virtual machine. However, no obvious indication can be seen from [Windows] Task Manager."
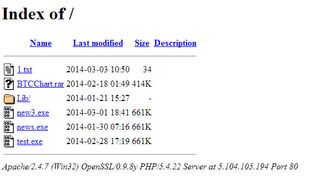
By using a packet sniffer, a software tool that analyzes Internet traffic, strongleaf saw that "the machine began to make connections to IP address 5.104.105.194 and attempts to download multiple malwares from the IP.
"By listing the directory index, the IP appears to host multiple files namely, news.exe, test.exe, BTCChart.rar," strongleaf wrote.
Tom's Guide was able to confirm strongleaf's observations, although we didn't try to install the fake Adobe Flash Player.
Needless to say, if you receive this message, don't click on the link, and don't install that bogus software, no matter how many bitcoins you lost when Mt. Gox went belly-up last week.
"Sites offering a faint ray of hope in the form of 'Mt. Gox is going to fix it all and please install this file, thanks' could well add more misery to an already considerable pile," Boyd noted.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.

