'Simjacker' Flaw Threatens 1 Billion Phones Worldwide
How to get your phone to give up your location

We're not halfway through September, but we've already got a prime candidate for Best Branded Bug of the Year.
Meet Simjacker, a vulnerability in how SIM cards for smartphones handle phone information. It's got its own logo (a mean-looking SIM card). It's got its own website. And its finder, Dublin-based Adaptive Security, evokes Dr. Evil in saying the flaw "could extend to over 1 billion mobile phone users globally."
So what is it? Well, Simjacker does not involve SIM-swapping, aka SIM-jacking, two common terms for when crooks talk a phone company into tranferring your mobile phone number to their SIM card so they can break into your online accounts. (Twitter CEO Jack Dorsey may have been a recent SIM-swap victim.) Nor is Simjacker a threat to most people, at least for right now.
MORE: Best Android Antivirus Apps
What it does is let specially crafted text messages silently force phones to text their geographical locations to other phones. It's being used by an unnamed spyware firm to track high-value targeted individuals on behalf of intelligence and police agencies around the world.
The targeted people have no idea the phones are giving up their locations. Of course, there are other ways to figure out a phone's location (American authorities can often get it from the phone companies), but this method is quick, easy and persistent once you get it set up.
How Simjacker works
Simjacker's modus operandi is pretty simple. An attacker's phone, or an attacker's computer rigged with SMS-sending hardware, sends a specially crafted text message to the SIM card on the targeted individual's mobile phone.
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.
Instructions in the text message make the SIM card retrieve the phone's location and device IDs, then send that data to another device controlled by or working with the attacker. In that way, any specific person whose mobile phone number is known to the attacker can be quickly located.
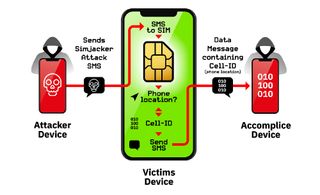
According to Adaptive Security, this works because of the SIM Application Toolkit (STK), a GSM standard that can give SIM cards a lot of power over the phones that use them.
Carriers can implement various parts of the toolkit according to their needs, but one commonly used tool is the S@T browser, which lets SIM cards access the internet on their own so that the STK can be updated over the air by specially composed text messages.
You may cringe at the prospect of phones secretly installing software on command from random texts. And you'd be right. But the S@T browser, first developed in 2009, has largely been forgotten as faster, more secure communications have been deployed, says Adaptive Security -- and yet it's still present on millions of phones.
Right now, says Adaptive Security, Simjacker is being used to only track locations, but other capabilities in the STK could let other malicious SMS messages make phone calls, disable the phone, open a mobile browser or even play ringtones.
What to do about Simjacker
Fortunately, you don't really need to do anything to combat this possible threat. The attack, as Adaptive Security says, requires a "[broad] range of specific SMS , SIM Card, Handset, Sim Toolkit , S@T Browser and SS7 knowledge to craft."
Adaptive Security expects more attacks of this type, but it's already working with its mobile-carrier customers around the world to detect and block Simjacker attacks, and it's passed on the information to the GSM Association to implement more security in the S@T browser. The company plans to present more details at the Virus Bulletin conference in London in early October.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.

